A security vulnerability in Ariane Allegro Hotel Check-In Kiosks exposed guest data and potentially compromised room access. However, a patch has been developed and is now available to address this issue, enhancing the security of the system
Pentagrid, a Swiss cybersecurity firm, recently uncovered a vulnerability in Ariane Allegro Scenario Player, a widely used software program in hotel check-in kiosks. The vulnerability could allow someone to exit the kiosk’s intended use (kiosk mode) and access the underlying Windows Desktop OS.
The software vendor, Ariane Systems, is a world leader in self-check-in and out solutions, serving 3,000 hotels and 500,000 rooms in over 25 countries.
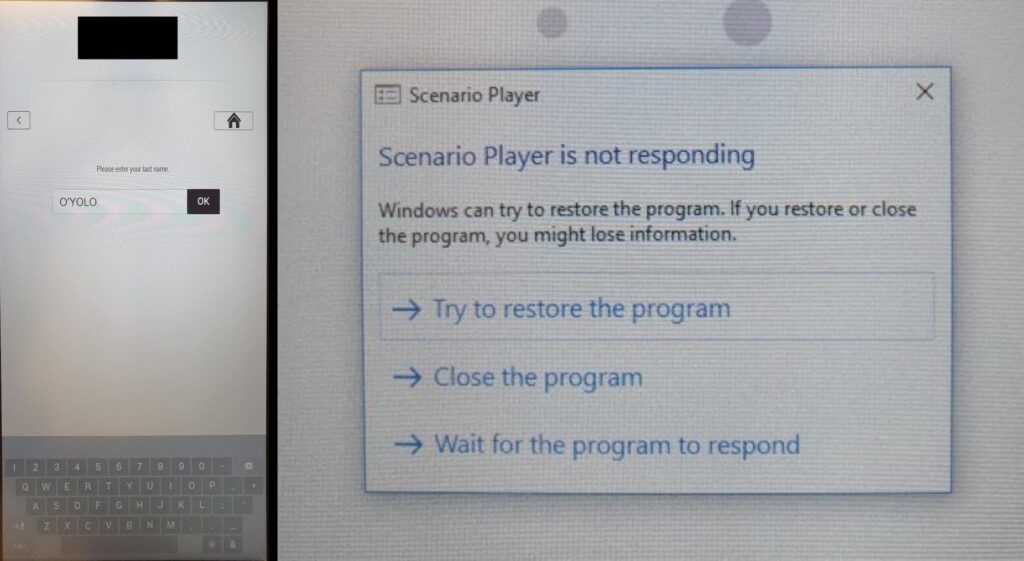
During a threat modelling workshop at a hospitality brand in Liechtenstein and Switzerland, Pentagrid’s Martin Schobert revealed that the app crashed in Kiosk mode after entering a single quote character into the guest search.
The hotel brand uses this check-in terminal, likely a type Ariane Duo 6000 series, for smaller locations to facilitate room booking/check-in, initiate payment via a POS terminal, provision RFID transponders to open the booked hotel room, and print invoices.
Schobert found that guests/users have to search for room reservations by entering booking code or surname. If the name contains a single-quote, such as “O’YOLO,” the application hangs, the Windows OS prompts the user to wait or stop the task, and selecting stop terminates the kiosk mode application.
When stopped, the Windows OS becomes accessible, which may have adverse consequences. such as allowing hotel network attacks, access to data stored on the terminal, including PII, reservations, and invoices, and RFID transponder allowing room keys to be created for other rooms. However, to exploit the flaw, the user must have physical access to the system, and the terminal must be in a self-service state, which hotels typically enable during specific times.
A CVE for the vulnerability is yet to be assigned whereas Kiosk Mode Bypass severity has been given as 6.3 (Medium). The vulnerability, discovered in March 2024, was promptly communicated to the vendor.
Ariane Systems clarified that these are “legacy systems,” in which the USB ports are disabled and “no PII or exploitable data can be retrieved from the kiosk.” Moreover, it believed the hotel must be using an outdated version of the software. However, Pentagrid asserted that the system’s design lets “the kiosk produces and keeps accessible invoice files.”
Nevertheless, Ariane Systems confirmed the issue has been fixed. However, the exact version fixing the issue isn’t publicly known. Hackread suggests contacting the vendor directly for clarification and installing the latest version immediately to stay protected.
John Bambenek, President of Cybersecurity and Threat Intelligence Consulting firm Bambenek Consulting commented on the issue emphasising the dangers of the potential access to victims’ rooms in domestic violence cases, theft of credit card data due to terminals doubling as POS devices.
“The biggest risk involves various domestic violence and stalking scenarios where unwanted guests could get keys to open a victim’s room. As these devices are also used as POS terminals to facilitate payments of hotel rooms, presumably the biggest risk there is stolen credit card information.“
“The underlying issue seems to be that the specific terminals at this specific location had the vulnerability (albeit, a very simple one to find) and later versions did not. Kiosks tend to be “set and forget” devices which means operators may not know they need to be updated on a routine basis…or if they are updated at all,“ he added.
“These devices probably cannot be completely isolated from the main hotel network as part of the point is to issue keys and handle room management, however, the devices should be limited to sending only required machines and ports with everything else filtered,“ Bambenek advised.