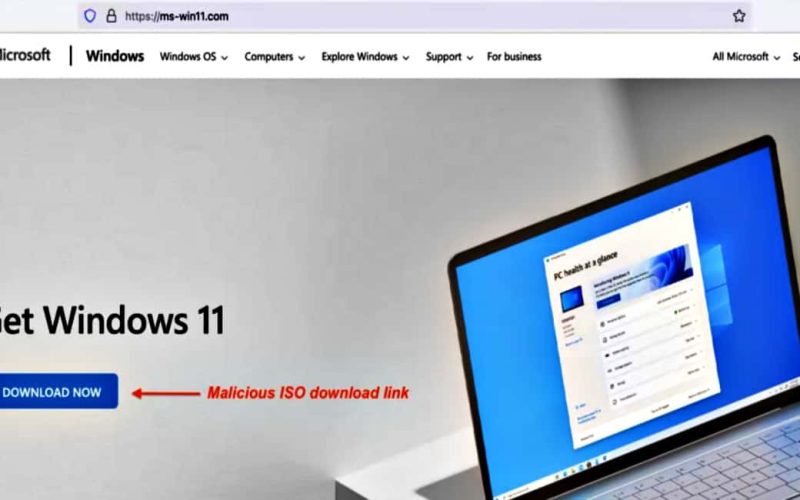
Phishing domains are spreading Windows 11 installers loaded with Vidar infostealer.
According to the cybersecurity firm Zscaler ThreatLabz, threat actors are trying to install info stealing malware on users’ devices through newly registered domains. Zscaler explained that these spoofed domains were first observed in April 2022 and created to distribute “malicious ISO files” (a PE32 binary) disguised as legit MS Windows 11 OS installers.
These malicious files deliver Vidar infostealer on the device. Some of the fake domains registered on 20 April include ms-win11com, win11-servcom, win11installcom, and ms-teams-appnet.
It is worth noting that Vidar malware was previously used in attacks against YouTubers and in a VPN scam in which a fake VPN website was discovered delivering password-stealing malware.
What is Vidar malware?
It is notorious info stealing malware that can perform spying on users. Its primary job is to steal sensitive user data such as operating system information, online accounts credentials, browser history, financial or banking data, and cryptocurrency wallet login details. It is generally distributed via the Fallout exploit kit.
How is Vidar Infostealer Distributed?
Vidar malware is delivered through phishing and attacker-controlled social media networks. ZScaler researchers noted that the Vidar malware variants extract the C2 configuration from these social media channels on the Mastodon network and Telegram.
In two cases examined by Zscaler, attackers created new user accounts and saved C2 server addresses in the profile section on Mastodon and Telegram channels. The same C2 was stored in the Channel Description tab. This helps attackers implant malware on vulnerable devices as these catch C2 configuration from the channels.
According to Zscaler’s blog post, those behind this campaign leverage backdoored versions of legitimate software like Adobe Photoshop and Microsoft Teams to distribute Vidar malware. Though the fake sites appear to be the central download portal, it is the ISO file that does the damage as it hides the malware payload and Themida.

This ISO file contains an unusually large-sized executable (more than 300MB) to avoid detection from anti-viruses. This file is signed with an expired certificate from Avast, and all binaries have been signed by a certificate featuring the same serial number.
Researchers believe that the certificate could be a part of the leaked data when Avast was targeted in October 2019. The ISO files, pretending to be Win 11 installers, also have a GitHub repository that stores the backdoored versions of Adobe Photoshop and other software.
More Windows 11 and Malware News
- Beware of Fake Windows 11 Update Delivering Malware
- Fake Windows 11 installers infecting devices with adware, malware
- Fake Windows website dropped Redline malware as Windows 11 upgrade
- 9-year-old Windows flaw abused to drop ZLoader malware in 111 countries
How to Stay Safe?
The best strategy to mitigate Vidar malware’s threat is downloading software from official websites and avoiding using cracked or free versions, as these are potential lures for exploitation.
“The threat actors distributing Vidar malware have demonstrated their ability to social engineer victims into installing Vidar stealer using themes related to the latest popular software applications. As always, users should be cautious when downloading software applications from the Internet.”
Sudeep Singh – Zscaler